-
Why IronNet
-
-
Use Cases
See how organizations benefit from IronNet
-
Customer Testimonials
See how customers benefit from IronNet
-
Industry Recognition
Discover what industry analysts are saying about Collective Defense and IronNet
-
For SOC Analysts
Reduce alert fatigue and build a more proactive defense
-
For CISOs
Maximize current investments and strengthen your security posture
-
Use Cases
-
-
NBH Bank draws on IronNet behavioral analytics for advanced threat detection
![IronNet-Case Study-NBH Bank]() Case StudyLearn more
Case StudyLearn more
-
NBH Bank draws on IronNet behavioral analytics for advanced threat detection
-
-
Platform
-
-
Collective Defense Platform
Leverage NDR powered by behavioral analytics and crowdsourced attack intelligence to secure your enterprise network
-
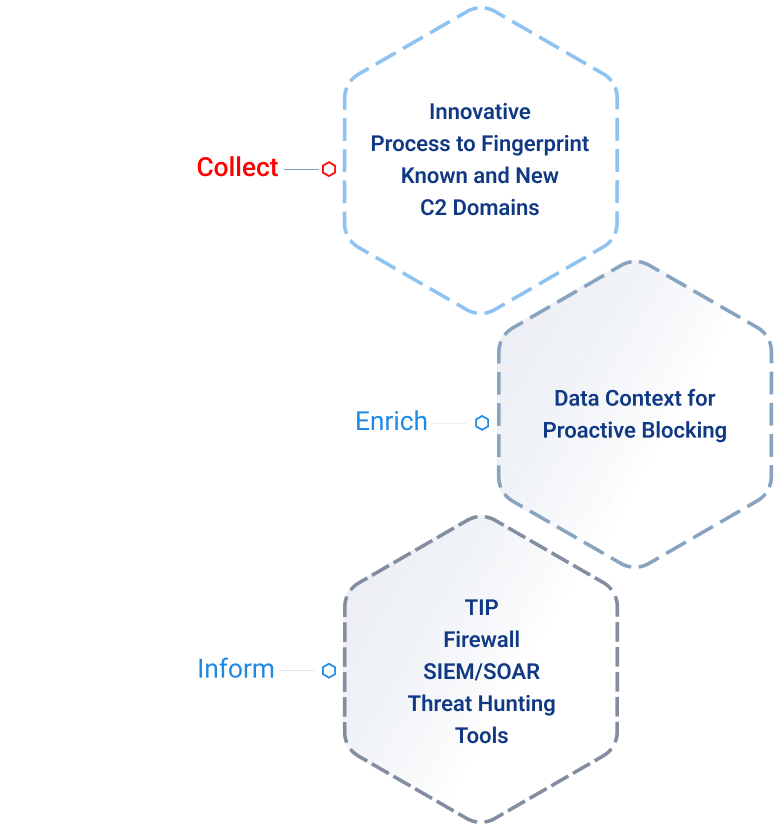
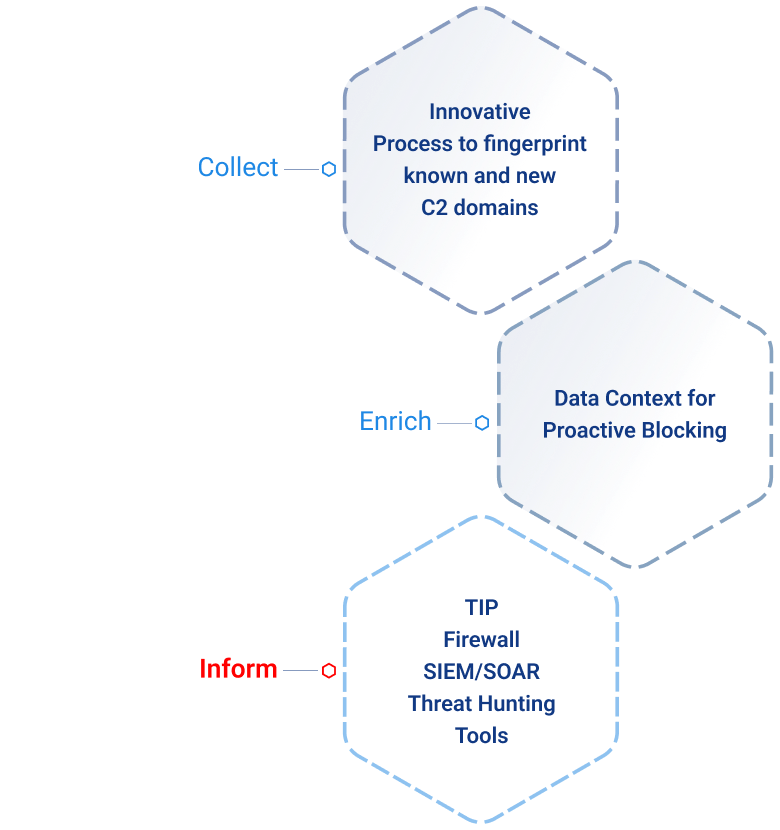
IronRadar Threat Intel Feed
Proactively block adversary infrastructure targeting your organization
-
Training
-
Collective Defense Platform
-
-
A practical way to rule out false positives
![A practical way to rule out false positives-WP Graphic]() EbookRead more
EbookRead more
-
A practical way to rule out false positives
-
- Industries
-
Company
-
-
8 Top Security Challenges
eBook...and ways IronNet customers are solving themDownload
-
8 Top Security Challenges
-
Resources
-
-
Biden Cyber EO
-
Cloud security
-
Collective defense
-
Cyber analytics
-
Cyber defense
-
Cyber risk
-
Cybersecurity strategy
-
Enterprise security
-
Extended Detection & Response (XDR)
-
MITRE ATT&CKⓇ Framework
-
Network Detection and Response (NDR)
-
Network security
-
Ransomware
-
Secure your supply chain
-
Security operations center (SOC)
-
Threat intelligence in cybersecurity
-
Biden Cyber EO
-
-
IronNet’s 2022 Annual Threat Report
![Group 287]() THREAT INTEL BRIEFSOur Annual Threat Report shares unique observations and analysis from our Threat Research Team.Read more
THREAT INTEL BRIEFSOur Annual Threat Report shares unique observations and analysis from our Threat Research Team.Read more
-
IronNet’s 2022 Annual Threat Report
- Request Demo
-
Why IronNet
-
-
Use Cases
See how organizations benefit from IronNet
-
Customer Testimonials
See how customers benefit from IronNet
-
Industry Recognition
Discover what industry analysts are saying about Collective Defense and IronNet
-
For SOC Analysts
Reduce alert fatigue and build a more proactive defense
-
For CISOs
Maximize current investments and strengthen your security posture
-
Use Cases
-
-
NBH Bank draws on IronNet behavioral analytics for advanced threat detection
![IronNet-Case Study-NBH Bank]() Case StudyLearn more
Case StudyLearn more
-
NBH Bank draws on IronNet behavioral analytics for advanced threat detection
-
-
Platform
-
-
Collective Defense Platform
Leverage NDR powered by behavioral analytics and crowdsourced attack intelligence to secure your enterprise network
-
IronRadar Threat Intel Feed
Proactively block adversary infrastructure targeting your organization
-
Training
-
Collective Defense Platform
-
-
A practical way to rule out false positives
![A practical way to rule out false positives-WP Graphic]() EbookRead more
EbookRead more
-
A practical way to rule out false positives
-
- Industries
-
Company
-
-
8 Top Security Challenges
eBook...and ways IronNet customers are solving themDownload
-
8 Top Security Challenges
-
Resources
-
-
Biden Cyber EO
-
Cloud security
-
Collective defense
-
Cyber analytics
-
Cyber defense
-
Cyber risk
-
Cybersecurity strategy
-
Enterprise security
-
Extended Detection & Response (XDR)
-
MITRE ATT&CKⓇ Framework
-
Network Detection and Response (NDR)
-
Network security
-
Ransomware
-
Secure your supply chain
-
Security operations center (SOC)
-
Threat intelligence in cybersecurity
-
Biden Cyber EO
-
-
IronNet’s 2022 Annual Threat Report
![Group 287]() THREAT INTEL BRIEFSOur Annual Threat Report shares unique observations and analysis from our Threat Research Team.Read more
THREAT INTEL BRIEFSOur Annual Threat Report shares unique observations and analysis from our Threat Research Team.Read more
-
IronNet’s 2022 Annual Threat Report
- Request Demo